Zero-Knowledge Proofs: The Magic Key to Identity Privacy
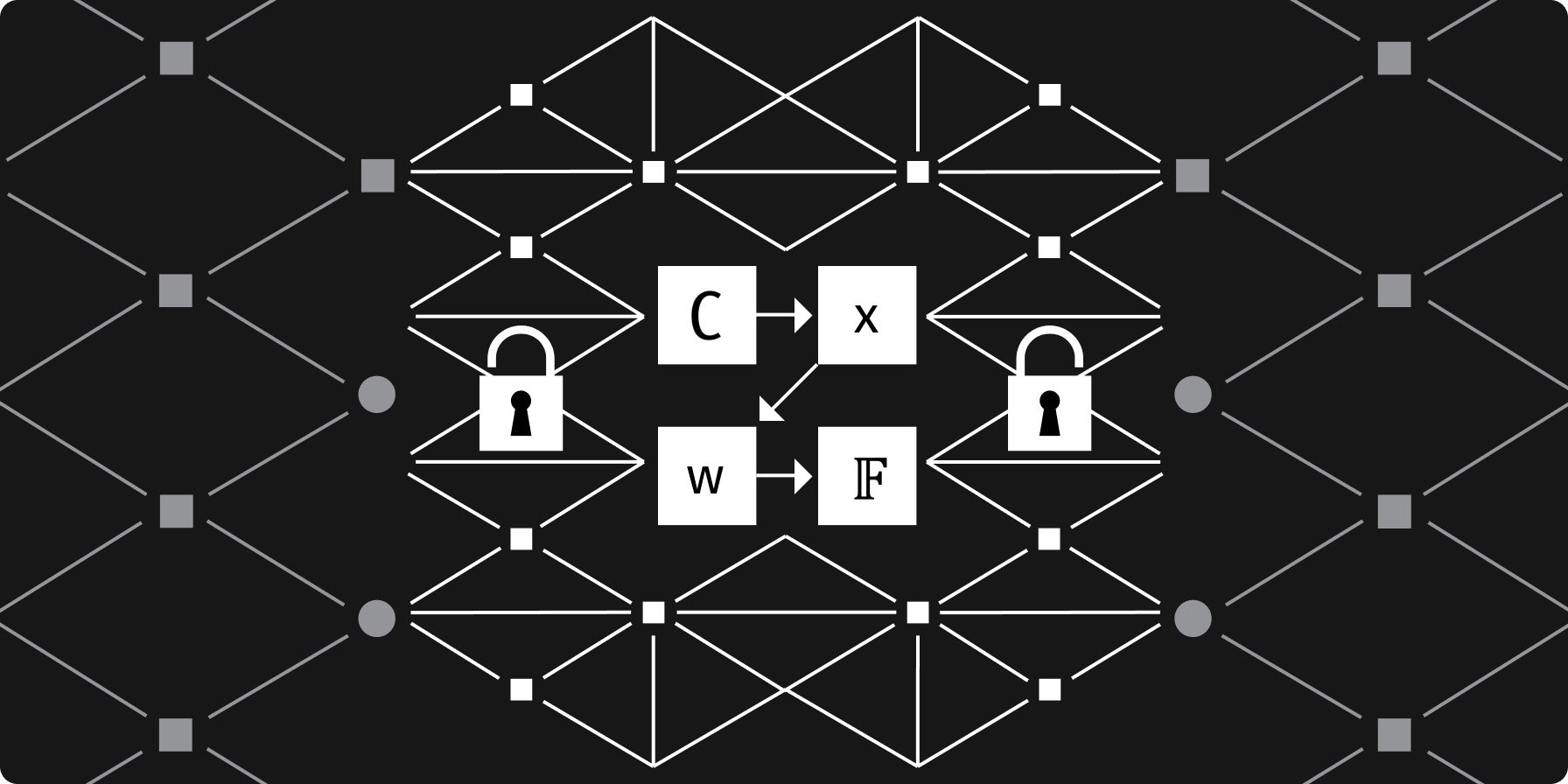
Among the many exciting potential applications for Zero Knowledge Proofs (ZKPs), one powerful use case is the ability to confirm specific identity attributes like age or citizenship, without revealing any other personal information, maintaining user privacy, and reducing the risk of identity theft or fraud.
The Magic Key to Your Digital Identity
In today's digital landscape, the security of our personal data is continually threatened by breaches and cyber-attacks. Zero-Knowledge Proofs (ZKPs), a revolutionary cryptographic technique formed a formidable line of defense for our digital identities. While the term "Zero-Knowledge Proofs" might seem abstract or even fantastical, it represents a cutting-edge approach to enhancing how we safeguard, manage, and engage with our online presence.
Originating from a 1985 paper, "The Knowledge Complexity of Interactive Proof Systems," the ZKP concept dictates that one party, the prover, can confirm the truth of a statement without revealing the actual statement.
Looking Inside Zero-Knowledge Proofs
At its core, ZKPs allow one party (the prover) to demonstrate to another party (the verifier) that an onchain statement is true without revealing any information about the statement itself. A famous example of this concept is the "Where's Waldo?" challenge. Here, the objective is for the prover to demonstrate they know Waldo's location without disclosing his exact spot on the page. To achieve this, the prover uses a board with a small hole sized precisely for Waldo. The prover covers the book with this board in such a way that only Waldo is visible through the hole. The verifier, upon looking through the hole, can confirm Waldo's presence but remains unaware of his exact position on the page. This method isn't a perfect representation of a zero-knowledge proof since it does give away some hints, like Waldo's body posture. Still, it aptly captures the foundational idea behind zero-knowledge proofs.
Beyond theoretical discussions, zero-knowledge proofs have practical significance in areas like cryptography, ensuring more secure passwords, digital signatures, and identities. In the context of identity verification, the prover wants to confirm a specific detail, such as their age or nationality, without giving away any other personal information. ZKPs use complex mathematical algorithms to create a digital "proof" that the verifier can trust without needing to see the actual underlying data.
Why ZKPs Shine in The Identity Space
In the physical world, proving your identity often means handing over a lot of sensitive data. With ZKPs, you can keep your treasure chest of personal information locked away. For example, you can prove age without revealing all the information on your driver’s license. ZKP enables you to do that. It verifies information while maintaining user privacy and reducing the risk of identity theft or fraud. Furthermore, ZKP can be used to fight misinformation, provide content provenance, and ensure more genuine interactions in a trust minimized environment.
ZKP Utility in the Real World
Smart Contract Applications: Onchain activity validation ZKPs can be applied to initiate smart contracts contingent on user actions without disclosing any personally identifiable information. This method operates akin to performing a cryptographic operation and observing the output without divulging the underlying computational processes. Use Cases:
A user can authenticate that they possess sufficient assets to complete a transaction without disclosing their overall account balance, thus enabling the execution of the smart contract in a secure and private manner.
A user can demonstrate eligibility for activities such as NFT creation or governance votes by providing evidence of past transactions.
A user can transfer their status and ranking between applications and blockchain networks to build and consolidate their reputation and score.
Financial Services: For institution and financial services, middleware that provides data privacy, enhanced security, and adherence to regulatory standards are critical. ZKPs can boost privacy by safeguarding client data while still maintaining regulatory adherence. In addition, they bolster security by keeping transaction specifics confidential, which minimizes potential data breaches. Furthermore, ZKPs have the capability to adhere to regulatory guidelines, all the while authenticating transactions and validating user identities.
User Insights: Organizations can use ZKPs to gain insights into user behavior without accessing personal data. For example, a company could use a ZKP to verify whether a user has watched a particular movie without knowing their entire viewing history. This enables targeted marketing without invading user privacy.
Decentralized Attestation: In the world of digital identity, ZKPs can also be used for decentralized attestation. This allows users to validate their attributes without exposing any personal information to the verifying party. Consider a scenario where you need to verify your employment status to get access to a restricted system. With a ZKP, you can confirm your employment without revealing where you work or any other details about your job. This means you can access the system securely without sharing any unnecessary information.
Why Now?
In today's digital era, the safeguarding of identity and efficient authentication are paramount. Traditional systems often expose personal details, but zero-knowledge proofs are a solution to this. It opens the possibility of sharing more by sharing less. It empowers individuals to retain control over their personal information, without hindering user experience. Especially for on-chain activities, zero-knowledge proofs streamline the authentication process, offering a repetitive use of a single proof and reducing data storage pressures. With the integration of zero-knowledge technology, blockchains can offload computations to coprocessors, and retain its security while scaling through mechanisms like zero-knowledge rollups.
The adoption of ZKPs in various use cases is currently hindered by the cold start problem, where the nascent phase of a new system sees limited or no utility due to initial barriers. The wider adoption of ZKP needs catalysts for the two-sided marketplace. To draw a parallel, consider the transformation Airbnb brought to the travel industry. Before its inception, the notion of staying in a stranger's home was largely alien and fraught with trust issues. Travelers faced skepticism due to the absence of brand assurance, while homeowners grappled with the risks of inviting unknown guests. The core issue was the lack of a reliable intermediary to bridge the trust gap between guests and hosts. Yet, with Airbnb's introduction of a credible platform offering features like liquidity discovery, trusted dispute mediation, insurance against unforeseen incidents, and transparent reviews, the once inconceivable became mainstream. Airbnb didn't merely offer an alternative to hotels; it expanded the horizons of travel.
Similarly, ZKPs empower individuals to disclose more information than they would otherwise be comfortable sharing, all while ensuring unparalleled privacy. These proofs provide verifiable data without revealing the specifics. For this potential to be fully realized, however, there's a need for mechanisms to meaningfully process this additional information at scale, enabling applications to refine their functionalities based on these insights. The overarching vision is to create a trust-minimized digital ecosystem, making the process of information sharing more streamlined. This will pave the way for a unified digital identity, ensuring seamless transitions across various platforms and bridging the gap between conventional web2 structures and the emergent web3 paradigm. However, the high computational cost associated with verifying these proofs can be a roadblock, restricting the range of viable applications and limiting user access. It's imperative to devise strategies to reduce both the computational expense and duration associated with generating and validating proofs, ensuring ZKPs are genuinely accessible for all. Various techniques are being actively explored by cryptographers to solve for this:
Recursion allows prover to verify the proof of another computation within a proof to maintain the succinctness.
Proof aggregation, homogeneous and eventually heterogeneous, would horizontally scale proving capability and amortize the cost for per proof verification.
Folding schemes like Nova, SuperNova and Sangria are utilized to create faster and easy to parallelize prover in untrusted setup supporting customizable circuits.
A ZKP Future
Zero-Knowledge Proofs represent a remarkable cryptographic advancement, offering a robust approach to managing digital identity securely and privately. As digital and onchain activities continue to permeate our lives, ZKPs present a method for preserving privacy and regulating access to personal information.
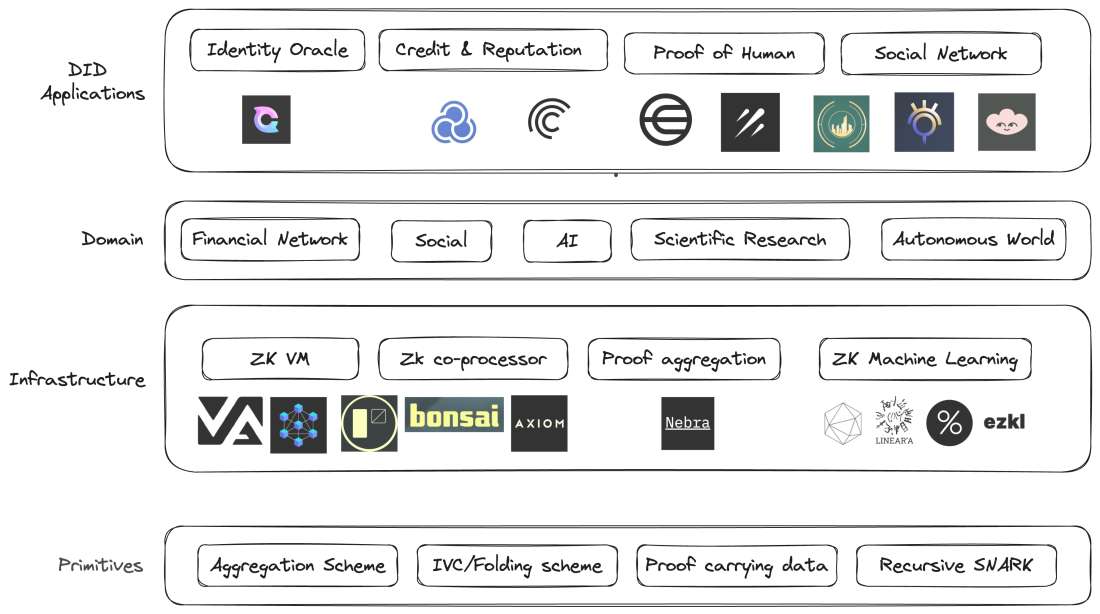
There are many interesting projects leveraging ZKP expanding the identity space with their innovations:
Clique is building privacy-preserving identity oracles that bring arbitrary web2 data on-chain in a fully confidential, tamper-proofed, and trust-minimized way.
Galxe is building an open and collaborative credential network with curation for web3 developers.
Sismo is offering sovereign single sign-on where apps can access previously unavailable data while maintaining user privacy.
Worldcoin seeks to create a global identity and financial network using "proof of personhood," ensuring each user is unique and human without revealing their real-world identity.
Zuzalu passport is an experimental passport uses zero-knowledge proofs to prove Zuzalu citizenship without revealing who you are.
To make ZKP more accessible to developers, many infrastructure companies are being built to improve the development experience:
Axiom is building the co-processor for trustlessly accessing and processing historical data.
Nebra is developing universal proof aggregation technologies to aggregate proofs generated from different circuits, proof systems to scale and lower the cost of ZKP verification.
Risczero, a portfolio company, is offering a general purpose zkVM, a high-performance tool for correct execution of arbitrary code.
The evolution of the concept of proof has philosophical implications on conviction and has catalyzed innovations once deemed unattainable. By adopting zero knowledge proof, it becomes possible to create an environment where digital identities are both secure and private, thus enabling individuals to share more online while still safeguarding their privacy. Moreover, with the rising concerns over surveillance and data breaches, ZKPs provide a beacon of hope for a more decentralized and user-centric internet.
The possibilities that ZKPs offer are not just confined to the realm of theoretical cryptography but are fast becoming an integral part of our digital ecosystems. From enabling more secure online voting systems to creating tamper-proof academic transcripts and beyond, the potential applications are vast and varied.
However, like all transformative technologies, the widespread adoption of ZKPs will require both technical evolution and societal acceptance. Developers and technologists must focus on making these solutions more intuitive and accessible, while end-users need to be educated about the benefits of this new paradigm.
In conclusion, the future of digital identity management is poised for a significant shift towards privacy and user control, thanks to zero-knowledge proofs. As we continue to explore and harness the power of ZKPs, one thing is clear: the promise of a safer, more private digital world is not just a distant dream, but a tangible reality on the horizon. It is up to us to embrace the emerging technology, champion its benefits, and shape a future where our digital selves are as protected as our real-world identities.



