Phishing Attacks Grow More Sophisticated

Even This Cybersecurity Veteran Almost Fell for One
Late last week, news emerged that a massive dataset had circulated online containing 16 billion user credentials, combining previously leaked information and newly obtained login data. It remains unclear who compiled the dataset or who re-released it. While much of the trove consists of repurposed data from past breaches, the inclusion of fresh credentials makes it particularly dangerous. This dataset is now considered one of the largest known single collections of compromised user accounts to date.
Hackers wasted no time exploiting the data through a variety of attack vectors. I was likely one of their targets.
The phishing attack I was hit with on June 19, directed at my personal (not Galaxy) devices and accounts, was the most sophisticated I have encountered in my career, including 10 years working in cybersecurity. The attackers first made it appear that my accounts were under active attack across multiple platforms, then followed up by impersonating Coinbase employees offering to help me stop it. They combined classic social engineering with coordinated tactics across text messages, phone calls, and spoofed emails—all designed to create a false sense of urgency, legitimacy, and scale. The fake attack felt widespread and authoritative, which is exactly what made the real one so convincing.
What follows is a detailed breakdown of how the attack unfolded, the red flags I noticed along the way, and the steps I took to protect myself. I will also share key lessons and practical recommendations to help digital asset investors stay safe as threats like this continue to evolve.
This incident demonstrates how older data, when combined with newly compromised credentials, can be used in highly targeted, multi-channel attacks. It reinforces the importance of layered security, clear user communication practices, and real-time response strategies. Institutions and individual users alike will find practical tools in this story, including verification protocols, domain awareness habits, and response steps that can help prevent a moment of confusion from turning into a major breach.
SIM Card Swap
The attack started around 3:15 p.m. Eastern time Thursday with a text message from an unidentified sender suggesting that someone was trying to trick a mobile carrier into transferring my phone number to someone else, an exploit known as a SIM swap.
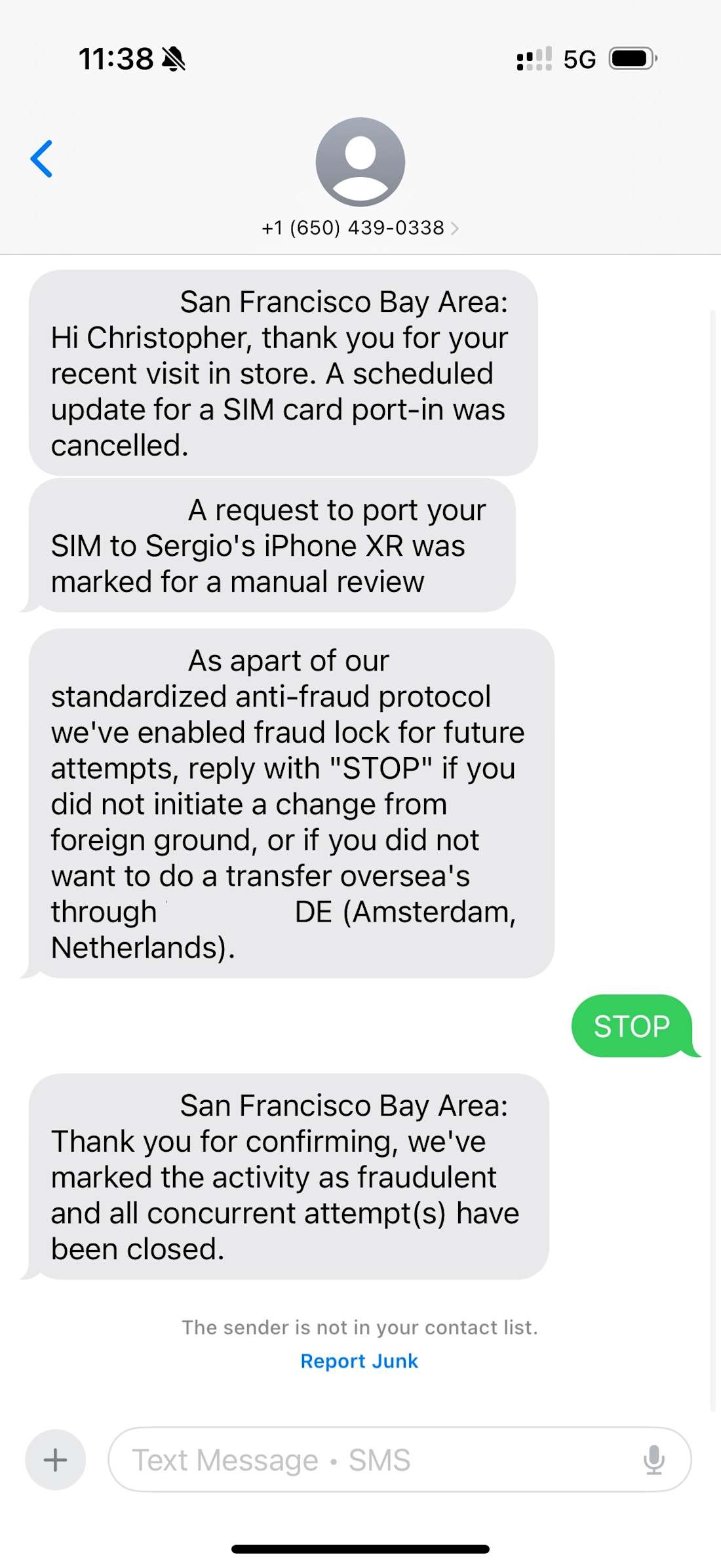
🚩You can see that this request did not come from a short code phone number, but rather a regular 10-digit number. Legit companies will use short codes when sending text messages. If you receive a text from an unknown, standard-length phone number that purports to be from a business, it is likely a scam or phishing attempt.
🚩The messages also contained conflicting information. The first message indicated that the transfer attempt was coming from the San Francisco Bay Area. A later message said it was happening in Amsterdam.
SIM swaps are very dangerous if successful, because attackers can obtain one-time codes that most companies employ to reset your password or access your account. This one wasn’t real, however; the hackers were priming me to fall for a more elaborate ruse.
One-Time Codes and Password Resets
The attack continued shortly thereafter, when I received one-time codes via text message and WhatsApp, supposedly from Venmo and PayPal. This was meant to foment uncertainty and make me believe someone was trying to log into my accounts at various money platforms. Unlike the suspicious-looking carrier messages, these did come from apparently legitimate short codes.
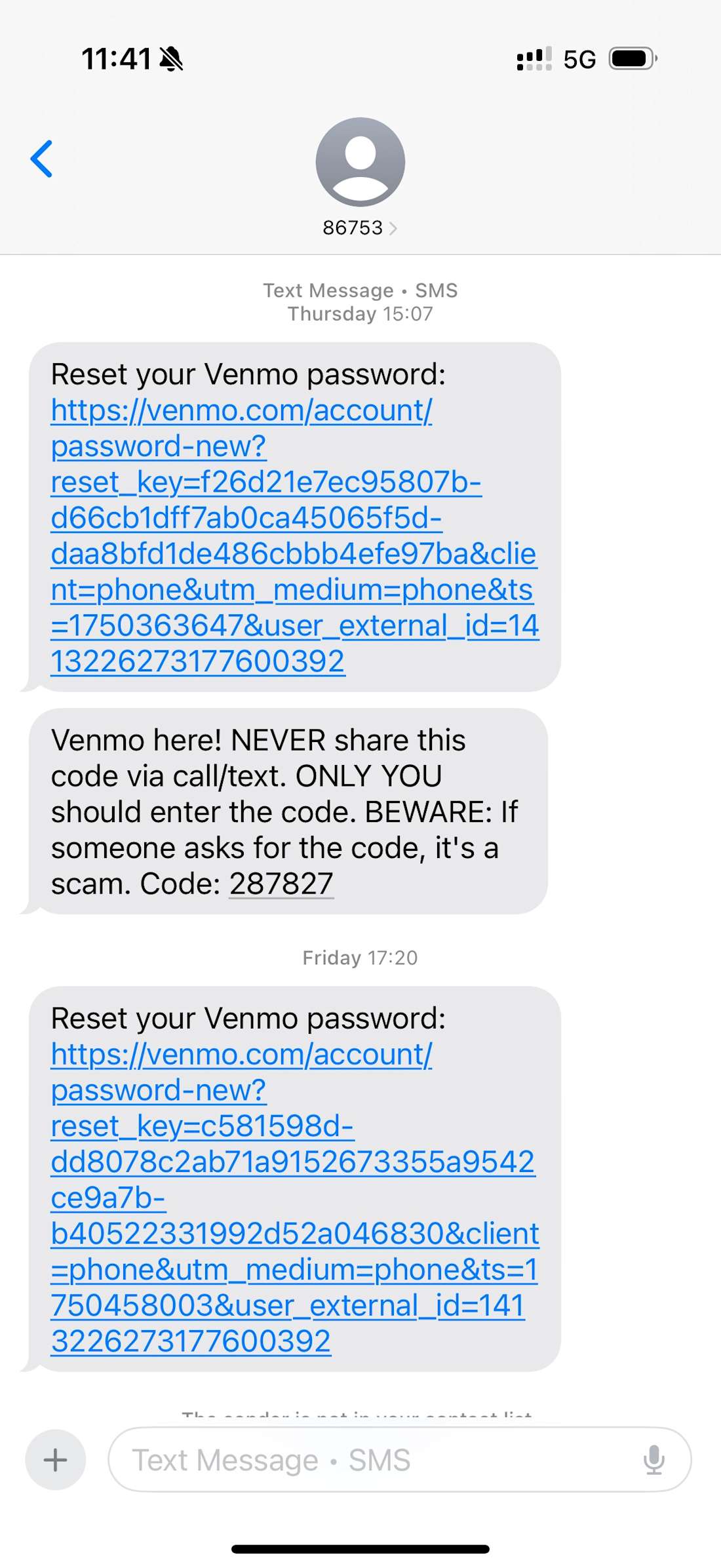
Coinbase Phishing Call
About five minutes after receiving the initial messages, I got a call from a California phone number. The caller, who identified himself as Mason, spoke with a perfect American accent. He claimed to be from the Coinbase Investigation team. In the past 30 minutes, he said, there had been over 30 attempts via Coinbase chat to reset my password and gain access to my account. According to "Mason,” the alleged attacker had passed the first round of security checks required for a password reset but failed the second layer of authentication.
He told me the individual was able to provide the last four digits of my Social Security number, my full driver’s license number, home address, and full name. However, they failed to provide the complete Social Security number, or the last four digits of the bank account or card connected to my Coinbase profile. This discrepancy, Mason explained, alerted Coinbase’s security team to contact me and take steps to contain the threat and stop the attack.
🚩A reputable exchange like Coinbase will never call you unprompted, unless you initiate a call through the support website. To find out more about the dos and don’ts of exchange customer support, read this Coinbase Documentation.
Security Check
After delivering the unwelcome news, Mason offered to secure my account by blocking additional attack vectors and access points into Coinbase. He began by focusing on my API connections and linked wallets, stating that he would revoke their access to reduce my overall exposure. He listed several connections, including Bitstamp, TradingView, MetaMask wallets, and a few others I didn’t recognize. I assumed I must have set those up and forgotten.
At this stage, my guard was down. I even felt reassured to hear Coinbase was taking proactive steps to protect my account.
Up to this point, Mason had not asked for any personal information, wallet addresses, two-factor authentication codes, or one-time passcodes, all things a phisher would typically ask for. The entire interaction felt secure and precautionary.
Subtle Pressure Tactics
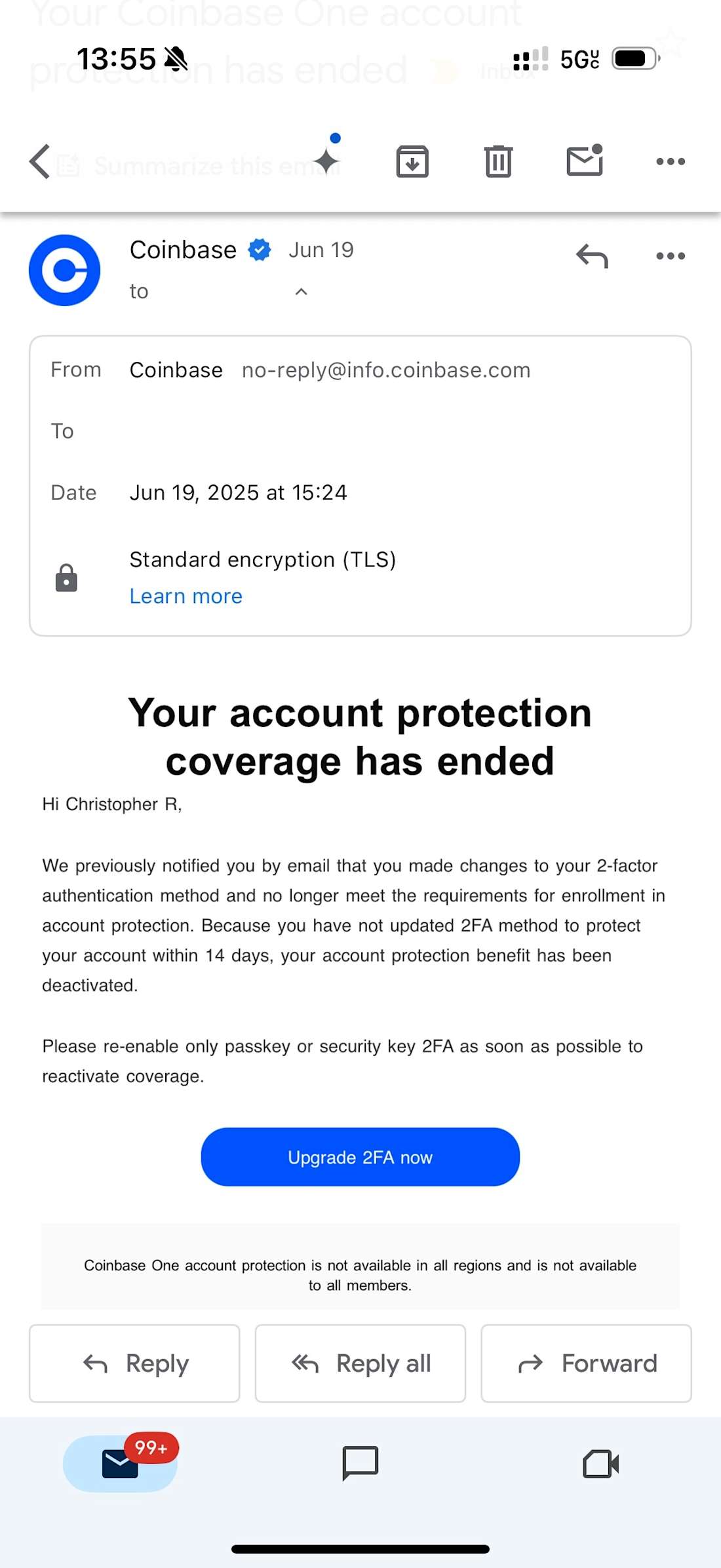
What came next was the first attempt to pressure me by creating a sense of urgency and vulnerability. After completing his "security check," Mason claimed that because my account had been flagged as high-risk, my account protection under the Coinbase One subscription service had been terminated. This meant any assets in my Coinbase wallet were no longer protected under FDIC insurance, he explained. If the alleged attackers succeeded in accessing the wallet and stealing funds, there would be no recourse. Neither Coinbase nor the government would reimburse me for the losses, Mason warned.
In retrospect, this line should have been a dead giveaway. Unlike bank balances, crypto assets are never FDIC-insured, and while Coinbase may hold customers’ dollars at FDIC-insured banks, the exchange itself is not an insured institution.
Mason also warned that a 24-hour countdown had begun, after which my account would be locked. Unlocking it, he said, would require a lengthy and complicated process. Furthermore, he said that if the alleged attackers somehow obtained my full Social Security number during that time, they could potentially bypass the lock and access my funds even while the account was frozen.
ℹ️ I later consulted with the real Coinbase support team, who informed me that locking your account is their recommended method to secure your account. Unlocking the account is a straightforward and secure process. You provide a photo of your ID and a selfie, and the exchange will verify it is you that is requesting an unlock and promptly restore access.
Next, I received two emails. The first was a subscription confirmation for Coinbase Bytes, the company’s newsletter, which the attackers triggered simply by submitting my email address through Coinbase’s public signup form. This appeared to be an attempt to flood my inbox with legitimate emails from Coinbase in order to build confidence and reinforce the legitimacy of their ongoing phishing scheme.
The second and more troubling email came from [email protected], stating that my Coinbase One account protection had been removed. The message came from what appeared to be a legitimate Coinbase domain. Had it come from a suspicious or unfamiliar domain, it would have been easy to dismiss. But because it appeared to originate from an official Coinbase address, it looked like the real deal.
Proposed Remediation Steps
Mason went on to suggest that to secure my account, we should lock my assets in a multi-signature wallet called Coinbase Vault. He implored me to Google “Coinbase Vault” and visit the Coinbase documentation around the service to quell my doubt that this was a legitimate service that Coinbase has offered for years.
I told him that I didn’t feel comfortable making such a drastic change without doing my due diligence. He agreed and encouraged me to take my time to research it thoroughly. I also insisted on contacting my mobile provider to protect my account from a potential SIM swap. He supported that decision and said I should handle it first. He told me he would call back in 30 minutes to continue with the next steps. After we ended the call, I received a text message confirming our conversation and the newly scheduled follow-up appointment.
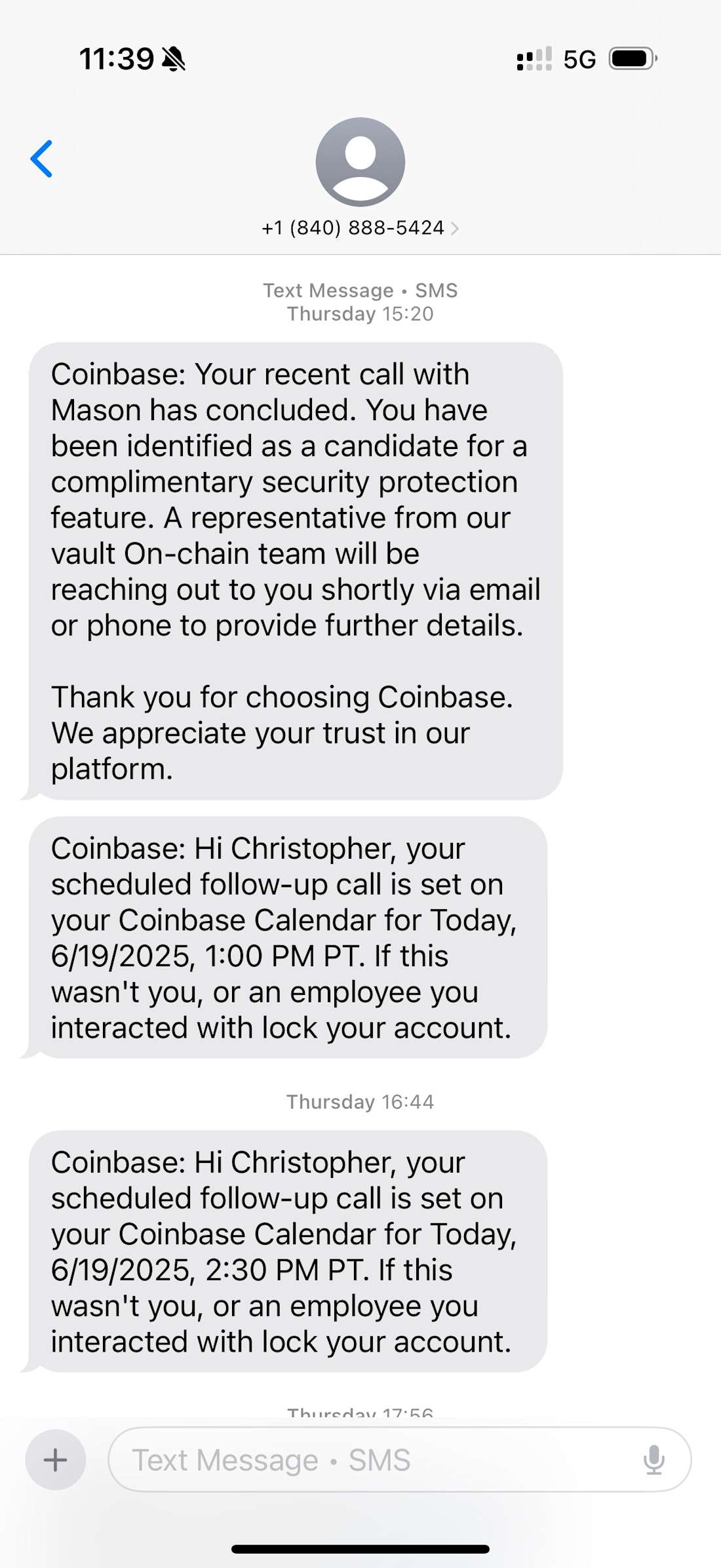
Follow-Up Call and Coinbase Vault
After contacting my mobile provider and confirming that no attempts had been made to transfer my SIM card, I proceeded to change the passwords for all my accounts. Shortly afterward, Mason called me back, and we began discussing the next steps.
During that time, I verified that Coinbase Vault is indeed a legitimate service offered by Coinbase. It is a multi-signature wallet solution designed to strengthen asset security by requiring additional signers to authorize transactions. However, it is not a self-custody solution. The assets remain in a Coinbase-managed hot wallet, but the multiple signature requirements and a 24-hour delay on withdrawals add layers of security. This setup is considered a hybrid model, offering more protection than a standard hot wallet, but it does not qualify as true cold storage.
Mason then provided me with a link, claiming it would allow me to review the security settings we had discussed during our first call. Once that review was complete, he said we could proceed with transferring my assets to the Coinbase Vault. This is when my instincts and cybersecurity experience kicked in.
Mason sent me a link to vault-coinbase.com and gave me a case number. When entered, the case number unlocked a portal that appeared to confirm the attempted account access and the API and third-party wallet connections we had supposedly “removed.” The process ended with a button labeled "Create Coinbase Vault."
At this point, I became suspicious. The domain looked off, and I began my own investigation.
First, I checked the website’s SSL certificate and noticed it had been issued only a month earlier, with no clear attribution to Coinbase. While SSL certificates can create the appearance of legitimacy, they are typically registered to verified companies, and this one lacked any formal association with Coinbase. That was a red flag that made me stop before taking any further action.
🚩Coinbase says it will never use a domain that is not officially associated with its own. If the company were to use a third-party service, it would more likely be hosted on a Coinbase subdomain, such as vault.coinbase.com. Additionally, any actions involving an exchange account should always take place through the company's official app or directly on its website.
I shared my concerns with Mason and told him that if I were to transfer my funds to the Coinbase Vault, I would only feel comfortable doing so through the official Coinbase app. He replied that using the app would result in a 48-hour delay for wallet creation and transfers. During that time, my account would still be locked within 24 hours, leaving it exposed and unprotected, because my Coinbase One protection had supposedly been removed.
I told him that I wasn’t willing to make such a significant change without careful consideration and additional research. He once again encouraged me to take my time and did not overtly pressure me to proceed. He said he would escalate the case to “Tier 3 Support" in the hopes they could reinstate my Coinbase One protection while I decided how to move forward.
I ended the call feeling frustrated and uneasy, and I continued verifying the security of all my other accounts.
'Tier 3 Support' Call
About half an hour later, I received a call from a Texas number. This caller, another individual who sounded American, claimed to be from the Tier 3 investigation team. He said he was following up on my request to reinstate Coinbase One account protection. According to him, the request had been escalated but would require a seven-day review process before approval. During that time, he warned, my account would remain uninsured and vulnerable to further attacks.
Mason’s apparent accomplice also claimed to be reviewing my assets and suggested that I might need to open different Vaults to secure assets across various blockchains. This gave me the impression that he had access to my account and was genuinely trying to help by recommending which Vaults I would need for each chain. In hindsight, however, he never mentioned any specific assets—instead, he referred vaguely to Ethereum, Bitcoin, and other blockchains.
He also mentioned that he was opening a ticket with the legal department to send me the chat transcript via email. Then, once again, he began encouraging me to use Coinbase Vault, which he described as the best option for securing my funds. As an alternative, he suggested a third-party wallet called SafePal, which he claimed would meet Coinbase’s security requirements and trigger reinstatement of my account protection. While SafePal is a legitimate hardware and software self-custody wallet, I now believe this suggestion was intended to build trust and make the push to transfer my assets to the malicious "Coinbase Vault" seem more credible.
I continued to express serious concerns about the vault-coinbase.com domain, but once again, the caller tried to assuage my worries. At that point, I believe the attackers realized they were not going to persuade me to transfer my assets and ultimately abandoned the phishing attempt.
Follow-up Call to Coinbase Support
After hanging up with the second bogus Coinbase rep, I went directly to Coinbase.com and submitted a support request to verify the attackers’ claims. I logged into my account, opened a support ticket, and was promptly contacted by a legit Coinbase representative. He confirmed that there had been no attempts to access my account or initiate any password resets.
He immediately advised me to lock my account and began gathering details about the attack, which he escalated to the real Coinbase investigation team. I provided all relevant information, including the fraudulent domains, phone numbers, and the attack vectors used, in the hope that the investigators would take swift action to investigate and mitigate the threat.
My primary concern was the Coinbase One Protection removal email, which came from [email protected]. I asked how it was possible for the attackers to spoof an email from a legitimate Coinbase domain. He acknowledged this was deeply concerning and assured me that Coinbase’s security team would investigate the issue thoroughly.
He also explained that locking your account is the most secure and recommended way to protect it in the event of a suspected breach. When it comes time to unlock the account, Coinbase uses a secure process that involves submitting a photo ID and a selfie, which are then verified against the information on file.
ℹ️ When contacting customer support at an exchange or custodian, always do so through official channels. A legit company like Coinbase will never reach out to you unprompted.
Takeaways
Fortunately, I did not fall victim to this phishing attempt. However, as a former cybersecurity professional, I found the near-miss deeply troubling. I believe that if it weren’t for my training and years of experience in the field, I might have been deceived. Had the attackers simply cold-called me, I would have ignored the call, and their attempt would have immediately failed. What made this phishing scheme effective was the series of coordinated false-flag tactics they used to create a sense of urgency and legitimacy.
While I took strong precautionary steps, I also fell for certain tactics. By reflecting on both, I hope to provide clear suggestions to help readers navigate and protect their assets in similar situations. With that in mind, let’s take a moment to review some of the red flags, key takeaways, and recommendations to help digital asset investors stay secure in today’s digital landscape.
Red Flags
🚩Coordinated false flag attempts creating confusion and urgency
The attackers began with a series of SIM card swap alerts and one-time code requests, purportedly from services like Venmo and PayPal. These came through both text message and WhatsApp and were designed to create the illusion that multiple platforms were under attack. These messages were likely triggered using only my phone number and email address—information that is unfortunately easy to obtain. I do not believe the attackers had access to any deeper account data at this stage.
🚩Use of both short codes and full-length phone numbers
The phishing messages were sent from a combination of SMS short codes and regular, full-length phone numbers. While companies typically use short codes for official communications, attackers can spoof or recycle them. However, legitimate services will never send security alerts from a standard phone number. Messages from full-length numbers should always be treated with skepticism.
🚩Requests to interact through unofficial or unfamiliar domains
The attacker asked me to visit a phishing site hosted on vault-coinbase.com, a domain that appears legitimate at first glance but is not affiliated with Coinbase. Always double-check the domain name and SSL certificate before entering any information. Actions related to sensitive accounts should only take place on the company’s official domain or app.
🚩Unprompted calls and follow-up communications
Coinbase, and most other financial institutions, will not call you unless you initiate a support request first. Receiving a phone call from someone claiming to be from a “Tier 3 Investigation Team” is a major red flag, especially when paired with scare tactics and complex instructions to protect your account.
🚩 Unsolicited Urgency and Consequences
Phishing attackers often use fear and urgency to push victims into acting without thinking. In this case, the threats of account lockout, asset theft, and the removal of insurance coverage were classic social engineering tactics.
🚩 Requests to Bypass Official Channels
Any suggestion to avoid using a company’s official app or website, especially when paired with a “faster” or “more secure” alternative, should set off alarm bells. Attackers may offer links that appear legitimate but redirect to malicious domains.
🚩Unverified Case Numbers or Support Tickets
Providing a “case number” that unlocks access to a custom-built phishing portal creates the illusion of legitimacy. No authentic service would require a user to validate their identity or take any action through a custom, external link with a case number.
🚩Mix of True and False Information
Attackers often blend real personal details (like email or partial SSN) with vague or inaccurate ones to appear credible. Any inconsistencies or vague references to “chains,” “wallets,” or “security reviews” should raise suspicion.
🚩Use of Real Company Names in Alternative Suggestions
Introducing trusted names like SafePal, even when they are legitimate, can be a misdirection tactic. It gives the illusion of choice and legitimacy while steering the victim toward a malicious action.
🚩Too Much Helpfulness Without Verification
The attackers acted patiently, encouraged me to do my own research, and did not initially ask for sensitive information. This behavior mimicked real support staff and made the scam seem professional. Any unsolicited support that seems “too good” should prompt skepticism.
Proactive Steps and Recommendations
ℹ️ Enable transaction-level verification for your exchange through push notifications or approval prompts
In your exchange settings, enable two-factor authentication and push-based verification. This ensures that any attempt to send or transfer funds requires a real-time confirmation sent to your trusted device, preventing unauthorized transactions.
ℹ️ Always reach out to service providers through legitimate, verified channels
In this case, I contacted my mobile provider and Coinbase directly by logging into official platforms and submitting a support request. This is the safest, and only appropriate way to engage with customer support staff when account security is at risk.
ℹ️ Exchange customer support agents will never ask you to move, access, or secure your funds
They will also never request or provide your wallet seed phrase, ask for your two-step verification code, or attempt to remotely access or install software on your devices.
ℹ️ Consider using multi-signature wallets or cold storage solutions to further secure your assets
Multi-signature wallets require multiple approvals to authorize a transaction, while cold storage keeps your private keys completely offline. Both are effective methods to protect long-term holdings from remote phishing or malware attacks.
ℹ️ Bookmark official URLs and avoid clicking on links from unsolicited messages
Typing the address yourself or using trusted bookmarks is the best way to avoid spoofed domains.
ℹ️ Use a password manager to detect suspicious sites and maintain strong, unique passwords across all accounts
Password managers help prevent phishing attempts by refusing to autofill on fake or unknown domains. Rotate passwords regularly and if you suspect any malicious attacks, immediately rotate your passwords.
ℹ️ Regularly review connected apps, API keys, and third-party integrations
Revoke access to any apps or services you no longer use or do not recognize.
ℹ️ Enable real-time account alerts wherever available
Notifications for sign-ins, withdrawals, or changes to security settings provide critical early warning of unauthorized activity.
ℹ️ Report all suspicious activity or communications to the service provider’s official support team
Early reporting can help prevent wider attacks and contributes to platform-wide security efforts.
Conclusion
For financial institutions, IT security teams, and executive leadership, this attack underscores how legacy data, when repurposed and combined with real-time social engineering, can be used to bypass even the most mature security environments. Threat actors are no longer relying on brute-force attacks alone, but are instead executing coordinated, cross-channel strategies that mirror legitimate workflows to gain trust and deceive users.
This calls for a broader focus, not only securing systems and networks, but also educating and empowering individuals to recognize threats and take action to protect themselves. People are often the front line of defense, and many employees carry risk across their professional and personal digital lives. Whether sitting on a trading desk or managing crypto assets at home, every individual must understand how personal compromise can metastasize into institutional exposure.
To stay ahead of these threats, institutions must invest in layered defenses, such as domain monitoring, adaptive authentication, phishing-resistant MFA, and clear communication protocols. Just as importantly, they must foster a culture of cybersecurity literacy, where every employee, from engineers to executives, understands their role in protecting the enterprise. In today’s environment, security is not just a technical function; it is a shared responsibility that extends from the individual to the organization as a whole.
Note: The interactions and communications referenced herein were conducted through personal email and telephone lines. They do not reflect or involve Galaxy corporate email accounts or business telephone lines.
Legal Disclosure:
This document, and the information contained herein, has been provided to you by Galaxy Digital Inc. and its affiliates (“Galaxy Digital”) solely for informational purposes. This document may not be reproduced or redistributed in whole or in part, in any format, without the express written approval of Galaxy Digital. Neither the information, nor any opinion contained in this document, constitutes an offer to buy or sell, or a solicitation of an offer to buy or sell, any advisory services, securities, futures, options or other financial instruments or to participate in any advisory services or trading strategy. Nothing contained in this document constitutes investment, legal or tax advice or is an endorsement of any of the stablecoins mentioned herein. You should make your own investigations and evaluations of the information herein. Any decisions based on information contained in this document are the sole responsibility of the reader. Readers should consult with their own advisors and rely on their independent judgement when making financial or investment decisions.
Participants, along with Galaxy Digital, may hold financial interests in certain assets referenced in this content. Galaxy Digital regularly engages in buying and selling financial instruments, including through hedging transactions, for its own proprietary accounts and on behalf of its counterparties. Galaxy Digital also provides services to vehicles that invest in various asset classes. If the value of such assets increases, those vehicles may benefit, and Galaxy Digital’s service fees may increase accordingly. The information and analysis in this communication are based on technical, fundamental, and market considerations and do not represent a formal valuation. For more information, please refer to Galaxy’s public filings and statements. Certain asset classes discussed, including digital assets, may be volatile and involve risk, and actual market outcomes may differ materially from perspectives expressed here.
For additional risks related to digital assets, please refer to the risk factors contained in filings Galaxy Digital Inc. makes with the Securities and Exchange Commission (the “SEC”) from time to time, including in its Quarterly Report on Form 10-Q for the quarter ended September 30, 2025, filed with the SEC on November 10, 2025, available at www.sec.gov.
Certain statements in this document reflect Galaxy Digital’s views, estimates, opinions or predictions (which may be based on proprietary models and assumptions, including, in particular, Galaxy Digital’s views on the current and future market for certain digital assets), and there is no guarantee that these views, estimates, opinions or predictions are currently accurate or that they will be ultimately realized. To the extent these assumptions or models are not correct or circumstances change, the actual performance may vary substantially from, and be less than, the estimates included herein. None of Galaxy Digital nor any of its affiliates, shareholders, partners, members, directors, officers, management, employees or representatives makes any representation or warranty, express or implied, as to the accuracy or completeness of any of the information or any other information (whether communicated in written or oral form) transmitted or made available to you. Each of the aforementioned parties expressly disclaims any and all liability relating to or resulting from the use of this information. Certain information contained herein (including financial information) has been obtained from published and non-published sources. Such information has not been independently verified by Galaxy Digital and, Galaxy Digital, does not assume responsibility for the accuracy of such information. Affiliates of Galaxy Digital may have owned, hedged and sold or may own, hedge and sell investments in some of the digital assets, protocols, equities, or other financial instruments discussed in this document. Affiliates of Galaxy Digital may also lend to some of the protocols discussed in this document, the underlying collateral of which could be the native token subject to liquidation in the event of a margin call or closeout. The economic result of closing out the protocol loan could directly conflict with other Galaxy affiliates that hold investments in, and support, such token. Except where otherwise indicated, the information in this document is based on matters as they exist as of the date of preparation and not as of any future date, and will not be updated or otherwise revised to reflect information that subsequently becomes available, or circumstances existing or changes occurring after the date hereof. This document provides links to other Websites that we think might be of interest to you. Please note that when you click on one of these links, you may be moving to a provider’s website that is not associated with Galaxy Digital. These linked sites and their providers are not controlled by us, and we are not responsible for the contents or the proper operation of any linked site. The inclusion of any link does not imply our endorsement or our adoption of the statements therein. We encourage you to read the terms of use and privacy statements of these linked sites as their policies may differ from ours. The foregoing does not constitute a “research report” as defined by FINRA Rule 2241 or a “debt research report” as defined by FINRA Rule 2242 and was not prepared by Galaxy Digital Partners LLC. Similarly, the foregoing does not constitute a “research report” as defined by CFTC Regulation 23.605(a)(9) and was not prepared by Galaxy Derivatives LLC. For all inquiries, please email [email protected].
©Copyright Galaxy Digital Inc. 2026. All rights reserved.



